In mid-June, US president Joe Biden held talks with his Russian counterpart Vladimir Putin to discuss a recent scourge of cyber attacks against the US, including by Russian-based criminal ransomware hackers.
Biden has said he told Putin in no uncertain terms that “certain critical infrastructure should be off limits to cyber attack — period”. Nevertheless, data show that ransomware attacks continue apace, including in sectors such as healthcare and education. It is unclear whether Biden will take further action in light of this.
Ransomware, which usually involves hackers seizing an organisation’s data or computer systems and only releasing access if a ransom is paid, has long plagued businesses large and small. The first known ransomware virus, PC Cyborg, was recorded in 1989, with victims infected via floppy disk and told to send a $189 cheque to an address in Panama.
Today, these financially motivated hacks are far more sophisticated — and are proliferating fast. Attacks have quadrupled during the pandemic, SonicWall data show, partly because the shift to remote working has left staff more vulnerable than if they were connecting to more secure corporate networks.

Additionally, hackers have swapped demanding cheques for requesting hard-to-track cryptocurrencies, meaning that as the price of bitcoin has risen during the past year, the business of ransomware has become all the more lucrative. It is also easier to launch attacks with little to no technical knowhow, given the growing market for “ransomware-as-a-service”, where hackers maintain their ransomware code but rent it out to others and take a cut of any extortion payouts.
While known attacks have reached unprecedented levels, the story of what we do not know — given that there are few rules around disclosure — may be far worse. Earlier this week, Bryan Vorndran, assistant director of the FBI Cyber Division and other cyber agency officials called for mandatory reporting rules around attacks, so that accurate data can be gathered and analysed by the US government.

Small businesses with little spare resources have tended to be the hardest hit by ransomware attackers. But the matter was thrust into the spotlight earlier this year after several audacious attacks on critical infrastructure such as the Colonial Pipeline, which led to fuel shortages for several days on the US east coast, the Irish health system and Brazilian meat supplier JBS. All of these attacks were believed to originate from Russia-based ransomware hackers, although the US government has accused Chinese state-backed groups of also orchestrating attacks.
The number of ransomware gangs stretches into the dozens and continues to proliferate as the economics remain so profitable. Vorndran said the FBI tracked 100 gangs, using an algorithm to rank them and the effect that each has on the economy. The largest one rakes in an estimated $200m a year in revenues, he said.
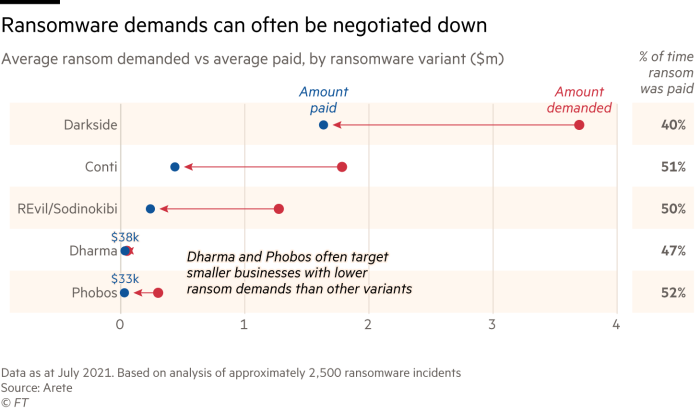
To help victims fight the gangs, a cottage industry for “ransomware negotiators” has emerged. These middlemen are tasked by victims with haggling down the ransom payments. As go-betweens, they also collect data on attacks, learning the playbooks of various groups in order to best know how to speak to them.
According to data from Coveware, the average ransom payment has fallen in the second quarter to $136,576, from more than $200,000 in the first quarter, amid an emergence of smaller ransomware groups. But in the majority of attacks — about 80 per cent — hackers are using the newer tactic of threatening to leak data as extra leverage in extorting victims. About half of these “leak threat” victims paid out in the second quarter, Coveware said.

Unfortunately, the negotiators’ services continue to be in high demand. According to data on reported attacks collated by Recorded Future, in the US there have been 10 attacks on healthcare, nine on schools and 10 on public state and local government groups during June and July this year. Despite Biden urging Putin last month to crack down on the criminal groups and warning against attacks on 16 critical entities, attacks on many of these key sectors have continued.
“The volume of targeted attacks on government organisations and enterprises that impact civilians, countries and the global economy will not end without a change in approach,” said Bill Conner, the chief executive of SonicWall.

